Example of Protected Health Information Cyber Awareness Challenge
For cybercriminals the healthcare industry is a golden goose. You must have your organizations permission to telework.

Dod Cyber Awareness Challenge 2020 Your Ultimate Guide Infosec Insights
Personal Identifying Information PII.

. Care by a covered entity that identifies or could. Health care provider related to the provision of health. Cyber Awareness Challenge 2022 Information Security.
How many potential insiders threat indicators does this employee display. Stolen protected health information PHI is worth hundreds even thousands of dollars on the black market. Sets with similar terms.
For example as one healthcare executive recently. The protected health information may exist in any form including on paper film and in electronic form. Explanation of benefits from a health insurance company.
Challenge people without proper badges. Protect your business and online security with these basic precautions that decrease your cyber security risks and align with HIPAAs Protected Health Information PHI guidelines. Keeping paper records containing PHI in locked cabinets.
Bob a coworker has been going through a divorce has financial difficulties and is displaying hostile behavior. A colleague complains about anxiety and exhaustion makes coworkers uncomfortable by asking excessive questions about classified projects and complain about the credit card bills that his wife runs up. When checking in at the airline counter for a business trip.
Use a classified network for all work especially unclassified processing. Cyber Awareness Challenge By. IBM reports that data breaches cost healthcare organizations an average of 713 million in their 2020 report.
Cyber Awareness Challenge 2021. Requests for Protected Health Information by persons or entities other than the patient should be directed to Medical Records. The Health Insurance Portability and Accountability Act HIPAA Security Rule ensures the protection of electronic health information with physical technical and administrative safeguards.
1 It also requires covered entities and business associates to implement cybersecurity awareness and training for all members of the workforce including. Removable media and devices include. What is the best example of Protected Health Information PHI.
The purpose of the Cyber Awareness Challenge is to influence behavior focusing on actions that authorized users can engage to mitigate threats and vulnerabilities to DoD Information Systems. Date and place of birth. Optical Discs Blu-Ray discs DVDS CD-ROMs Memory Cards Compact Flash card Secure Digital card Memory Stick Zip Disks Floppy disks.
Ensuring that laptops are never left in unsafe places. Protected health information is a form of individually identifiable health information. Time-to-report and time-to-discover periods are often long giving cybercriminals ample time to collect and sell stolen records online before vulnerabilities are detected and.
Label all files removable media and subject headers with appropriate classification markings. As an agency or any institution that relays PHI you have observed firsthand the integration of new technology and its positive impact within the insurance industry. DOD Cyber Awareness Challenge 2019.
Protected Health Information PHI. Some examples of removable media are memory sticks. Decline to lend the man your phone.
The Cyber Awareness Challenge which is also known as the Army Cyber Awareness Training the cyber awareness challenge or the DOD cyber challenge is an annual computer security training that was created to increase cyber awareness among. Be aware of the network you are using when connecting a personal unauthorized device. If your organization allows it.
Sensitive data such as protected health information PHI and electronic medical records EMR. 2020 Cyber Awareness Challenge. Decline so that you maintain physical contact of your Government-issued laptop.
_____ protected health information Cyber awareness challenge 2021 Examples of PHI can include. An EHR alters the mix of security. What Are Some Examples Of Removable.
The definition of PHI includes the form of the data. Using robust access control to physical areas that may contain large amounts of PHI data eg server rooms Technical. ActiveX is a type of this.
With this in mind lets explore five of the cybersecurity challenges in healthcare to get a clearer image of the industrys. This article will provide you with all the questions and answers for Cyber Awareness Challenge. The use of the phrase electronic PHI ePHI has become more popular with the rise of digital information.
Your health insurance explanation of benefits EOB. What should you do. Protected Health Information PHI.
BitGlass reports that 673 of all healthcare breaches in 2020 were caused by hacking and IT incidents. 10 How many types of spill are there. Names All elements of dates other than year directly related to an individual including birth dates.
Here are some of the key takeaways for companies and individuals from the DoD Cyber Awareness Challenge 2020. Other sets by this creator. This training is current designed to be engaging and relevant to the user.
Which of the following is the best example of Protected Health Information PHI. Identify the different types of information and the requirements to protect each content typefor example classified information personally identifiable information protected health information Identify the different forms and methods of cyber attacksfor example social engineering email phishing viruses. No matter how secure a healthcare providers systems are theres one vulnerability that even the best technology in the world cant address.
The HIPAA Security Rule 45 CFR Part 160 and Part 164 Subparts A and C sets forth requirements for electronic protected health information. A man you do not know is trying to look at your Government-issued phone and has asked to use it. Your health insurance explanation of benefits EOB What does Personally Identifiable Information PII include.
Is a subset of PII requiring additional protection Is health information that identifies the individual Is created or received by a healthcare provider health plan or employer or a business associate of these Relates to. Cyber Awareness 2020 Knowledge Check. Which of the following is an example of Protected Health Information PHI.
Health information that is created or received by a. All https sites are legitimate and there is no risk to entering your personal info online. Mothers maiden name What is a good practice for physical security.
The Cyber Awareness Challenge is the DoD baseline standard for end user. Using encryption such as full-disk encryption on laptops that contain any PHI. Protected Health Information PHI is an individuals.
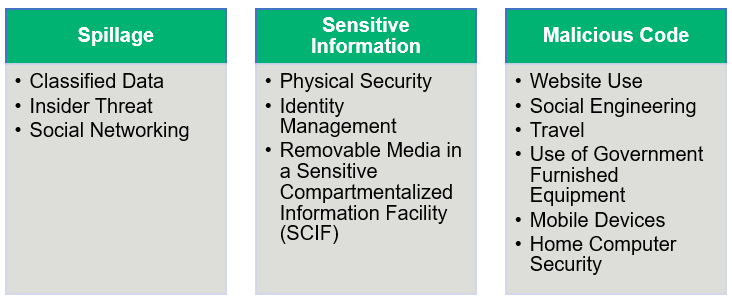
Dod Cyber Awareness Challenge 2020 Your Ultimate Guide Infosec Insights

Hackers Selling Healthcare Data In The Black Market Infosec Resources

Premium Vector Fingerprint Recognition Technology For User Id Security Finger Touch Scanner App To Secure Personal Information Data Cyber Security Protectio Cyber Security Fingerprint Recognition Scanner App

4 Must See Examples Of Gamification Of Compliance Training Infographic E Learning Infographics Gamification Instructional Design Elearning
No comments for "Example of Protected Health Information Cyber Awareness Challenge"
Post a Comment